They use the same Key ID. It is the key identifier and not the key. it identifies the key it was encrypted with.
The same content(movie or specific episode) was using the same keyID in the files. So that indicated they were encrypted with the same key. That is the whole point of what I have been attempting.
The decryption could be failing because I didn't implement the IV counter for AES_CTR correctly. They use a 64bit IV. It is expaned to 128bit by padding. I am not sure I did that right.
I thought maybe we could get the apple media play to play it correctly. The "#EXT-X-MAP:URI=" value needs to be changed to the name of the local video file UVD downloads. It is actually pointing to data embedded in the file.(length:2067 @ offset 0)
the "#EXT-X-KEY:METHOD=" value of ISO-23001-7 indicates a CENC(Common Encryption) for the video. I thought maybe we could bypass the key delivery by changing the URI to the local key file. I could never get it working. I am not sure if I should remove or change the value of the keyformat.
Quote:
Originally Posted by krystallinity
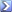
#EXTM3U
#EXT-X-KEY:METHOD=ISO-23001-7,
URI="f10niQg0DsZqw5uIro8MDucooPo=",
KEYFORMAT="com.apple.streamingkeydelivery",
KEYFORMATVERSIONS="1"
#EXT-X-MAP:URI="http://23.246.6.145/?o=AQGST62xhTHsk1jsUJHdtSI4ryVV4kye3ZFYFbTgvJKrhw3 SkDEAulihIXOeFm662b7G4n4UiY0e4_ElClKi6g9te9cfl2m6k 2FKRT8dtMS5SlhYArKXZV4Z1BVEKWdaBRxgHbg&v=3&e=14100 65726&t=2-KEygddY3nVRFovfQcFObAptDg",
BYTERANGE="2067@0"
|
Quote:
|
#EXT-X-KEY:METHOD=AES-128,URI="crypt0.key"
|
The files also have header values that indicate wedevine(google) drm support. I really think this format is going to be used in their future for a while.
Edit: I'm an idiot. I misread the Kids. It is actually incremented by 1. The decryption was simply failing because the key was wrong.
00000000-03C1-23FC-0000-000000000000
00000000-03C1-23FD-0000-000000000000